Azure Cloud Security Risks Explained 2024
Regardless of any great advantages offered by different cloud providers, saving a company’s workloads to a public cloud serviced exposes the organization to new data security risks. Here are the top cloud computing security risks that every firm faces.
Theft or loss of intellectual property
Admins employing very weak security measures within an organization that include storing data without encryption or failing to install other authentication protocols to gain access to the service.
Malware attacks
Once a system is compromised by cloud malware, the cloud security risks increase dramatically as the malware executes. In some cases, it may begin siphoning out sensitive or protected data, such as customer financial information. Malware can cause more than just a downed device. In fact, it can lead to large-scale data exfiltration and all the consequences that that incur.
Compliance violations and regulatory actions
These days, most companies operate under some sort of regulatory control of their information, whether it’s HIPAA for private health information, confidential student records, or one of many other government and industry regulations. Under these mandates, companies must know where their data is, who is able to access it, and how it is being protected.
End-user Control If proper end user control is not employed, the staff could be sharing just about anything to public domains or for their personal gains later.
Contract breaches with clients and/or business partners
Contracts restrict how business partners or clients use data and also who has the authorization to access it. If this is not audited, any staff who shares that information put himself and the firm at risk of legal action without permission from the relevant authorities.
Insecure interfaces and APIs
Cloud is new and rapidly evolving, so lots of new, insecure APIs surface. This includes weak TLS crypto or incomplete verification of encrypted content. The responsibility to address this threat lies with both cloud providers and users.
Denial of service (DOS)
Denial of service attacks, unlike cyber-attacks, do not attempt to bypass your security protocol. Instead, they make your servers unavailable to illegitimate users. DOS also results in a non-operational environment for your firm causing revenue loss as well for hours or days.
Diminished customer trust
Data breaches inevitably result in diminished trust by customers. The breach lets customers to stay away from stores or websites, and will result in loss of business for the company.
Increased customer loss
If customers even suspect that their data is not fully protected by enterprise-grade security controls, they may take their business elsewhere to a company they can trust.
Azure Security Standards for Cloud risks
Here’s a closer look specific security features that Microsoft Azure employs to offer industryleading security, privacy, and compliance. This article provides a comprehensive look at the security available with Azure
Applications
The section provides additional information regarding key features in application security and summary information about these capabilities.
Web Application vulnerability scanning
Azure APP service provides testing for vulnerabilities on your App Service app with Tinfoil Security to perform one-click vulnerability scanning on your app. You can view the test results in an easy-to-understand report, and learn how to fix each vulnerability with step-by-step instructions.
Penetration Testing
If you prefer to perform your own penetration tests or want to use another scanner suite or provider, you must follow the Azure penetration testing approval process and obtain prior approval to perform the desired penetration tests.
Web Application firewall
The web application firewall (WAF) in Azure Application Gateway helps protect web
applications from common web-based attacks like SQL injection, cross-site scripting attacks, and session hijacking. It comes preconfigured with protection from threats identified by the Open Web Application Security Project (OWASP) as the top 10 common vulnerabilities.
Authentication and authorization in Azure App Service
App Service Authentication / Authorization is a feature that provides a way for your
application to sign in users so that you don’t have to change code on the app backend
Storage
The section provides additional information regarding key features in Azure storage security and summary information about these capabilities.
Role-Based Access Control (RBAC)
You can secure your storage account with Role-Based Access Control (RBAC). Restricting
access based on the need to know and least privilege security principles is imperative for
organizations that want to enforce security policies for data access.
Shared Access Signature
A shared access signature (SAS) provides delegated access to resources in your storage
account. The SAS means that you can grant a client limited permission to objects in your
storage account for a specified period and with a specified set of permissions.
Encryption in Transit
Encryption in transit is a mechanism of protecting data when it is transmitted across networks and it is provided natively by Azure.
Encryption at rest
For many organizations, data encryption at rest is a mandatory step towards data privacy, compliance, and data sovereignty and it is provided natively by Azure.
Storage Analytics
Azure Storage Analytics performs logging and provides metrics data for a storage account. You can use this data to trace requests, analyse usage trends, and diagnose issues with your storage account. Storage Analytics logs detailed information about successful and failed requests to a storage service
Enabling Browser-Based Clients Using CORS
Azure storage services now support CORS so that once you set the CORS rules for the service,a properly authenticated request made against the service from a different domain is evaluated to determine whether it is allowed according to the rules you have specified.
Networking
The section provides additional information regarding key features in Azure network security and summary information about these capabilities.
Network Security Groups
A Network Security Group (NSG) is a basic stateful packet filtering firewall and it enables you to control access based on a 5-tuple. NSGs do not provide application layer inspection or authenticated access controls. They can be used to control traffic moving between subnets within an Azure Virtual Network and traffic between an Azure Virtual Network and the Internet.
Route Control and Forced Tunnelling
User-Defined Routes allow you to customize inbound and outbound paths for traffic moving into and out of individual virtual machines or subnets to insure the most secure route possible. Forced tunnelling is a mechanism you can use to ensure that your services are not allowed to initiate a connection to devices on the Internet. For example, if you want to make sure that all traffic to and from your Azure Virtual Network goes through that virtual security appliance, you need to be able to control and customize routing behaviour. You can do this by configuring User-Defined Routes in Azure.
Virtual Network Security Appliances
There may be times when you want to enable security at higher levels of the networking stack. You can access these enhanced network security features by using an Azure partner network security appliance solution.
Azure Virtual Network
An Azure virtual network (VNet) is a representation of your own network in the cloud. It is a logical isolation of the Azure network fabric dedicated to your subscription. You can fully control the IP address blocks, DNS settings, security policies, and route tables within this network. You can segment your VNet into subnets and place Azure IaaS virtual machines (VMs) and/or Cloud services (PaaS role instances) on Azure Virtual Networks.
VPN Gateway
To send network traffic between your Azure Virtual Network and your on-premises site, you must create a VPN gateway for your Azure Virtual Network. A VPN gateway is a type of virtual network gateway that sends encrypted traffic across a public connection. You can also use VPN gateways to send traffic between Azure Virtual Networks over the Azure network fabric.
Express Route
Microsoft Azure ExpressRoute is a dedicated WAN link that lets you extend your on-premises networks into the Microsoft cloud over a dedicated private connection facilitated by a connectivity provider. ExpressRoute connections do not go over the public Internet and thus can be considered more secure than VPN-based solution.
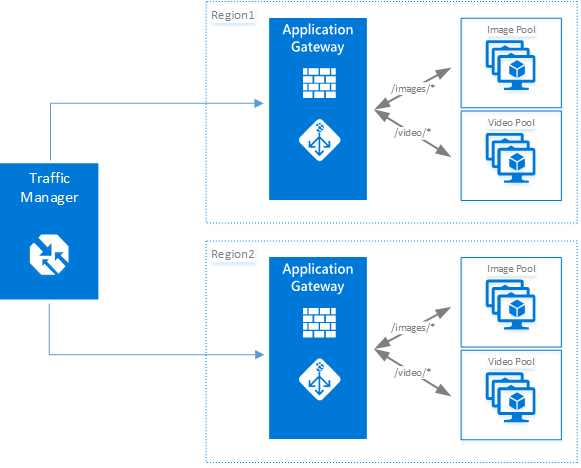
Application Gateway
Microsoft Azure Application Gateway provides an Application Delivery Controller (ADC) as a service, offering various layer 7 load balancing capabilities for your application. It allows you to optimize web farm productivity by offloading CPU intensive TLS termination to the Application Gateway (also known as “TLS offload” or “TLS bridging”). It also provides other Layer 7 routing capabilities including round-robin distribution of incoming traffic, cookie- based session affinity, URL path-based routing, and the ability to host multiple websites behind a single Application Gateway. Azure Application Gateway is a layer-7 load balancer. It provides failover, performance-routing HTTP requests between different servers, whether they are on the cloud or on-premises.
Web Application Firewall
Web Application Firewall is a feature of Azure Application Gateway that provides protection to web applications that use application gateway for standard Application Delivery Control (ADC) functions. Web application firewall does this by protecting them against most of the OWASP top 10 common web vulnerabilities.
Traffic Manager
Microsoft Azure Traffic Manager allows you to control the distribution of user traffic for service endpoints in different data centers. Service endpoints supported by Traffic Manager include Azure VMs, Web Apps, and Cloud services. You can also use Traffic Manager with external, non-Azure endpoints. Traffic Manager uses the Domain Name System (DNS) to direct client requests to the most appropriate endpoint based on a traffic-routing method and the health of the endpoints.
Azure Load Balancer
Azure Load Balancer delivers high availability and network performance to your applications. It is a Layer 4 (TCP, UDP) load balancer that distributes incoming traffic among healthy instances of services defined in a load-balanced set.
Azure Security Center
Azure Security Center continuously analyzes the security state of your Azure resources for network security best practices. When Security Center identifies potential security vulnerabilities, it creates recommendations that guide you through the process of configuring the needed controls to harden and protect your resources.
Azure Compute
The section provides additional information regarding key features in this area and summary information about these capabilities.
Antimalware & Antivirus
With Azure IaaS, you can use antimalware software from security vendors such as Microsoft, Symantec, Trend Micro, McAfee, and Kaspersky to protect your virtual machines from malicious files, adware, and other threats. Microsoft Antimalware for Azure Cloud Services and Virtual Machines is a protection capability that helps identify and remove viruses, spyware, and other malicious software.
Hardware Security Module
Encryption and authentication do not improve security unless the keys themselves are protected. You can simplify the management and security of your critical secrets and keys by storing them in Azure Key Vault. Key Vault provides the option to store your keys in hardware Security modules (HSMs) certified to FIPS 140-2 Level 2 standards.
Virtual machine backup
Azure Backup is a solution that protects your application data with zero capital investment and minimal operating costs. With Azure Backup, your virtual machines running Windows and Linux are protected.
Azure Site Recovery
An important part of your organization’s business continuity/disaster recovery (BCDR) strategy is figuring out how to keep corporate workloads and apps up and running when planned and unplanned outages occur. Azure Site Recovery helps orchestrate replication, failover, and recovery of workloads and apps so that they are available from a secondary location if your primary location goes down.
SQL VM TDE
Transparent data encryption (TDE) and column level encryption (CLE) are SQL server encryption features. This form of encryption requires customers to manage and store the cryptographic keys you use for encryption.
VM Disk Encryption
Azure Disk Encryption is a new capability that helps you encrypt your Windows and Linux IaaS virtual machine disks. It applies the industry standard BitLocker feature of Windows and the DM-Crypt feature of Linux to provide volume encryption for the OS and the data disks.
Patch Updates
Patch Updates provide the basis for finding and fixing potential problems and simplify the software update management process, both by reducing the number of software updates you must deploy in your enterprise and by increasing your ability to monitor compliance.
Identity and access management
Microsoft uses multiple security practices and technologies across its products and services to manage identity and access.
- Multi-Factor Authentication requires users to use multiple methods for access, on- premises and in the cloud.
- Microsoft Authenticator provides a user-friendly Multi-Factor Authentication experience that works with both Microsoft Azure Active Directory and Microsoft accounts, and includes support for wearables and fingerprint-based approvals.
- Password policy enforcement increases the security of traditional passwords by imposing length and complexity requirements, forced periodic rotation, and account lockout after failed authentication attempts.
- Token-based authentication enables authentication via Azure Active Directory.
- Role-based access control (RBAC) enables you to grant access based on the user’s assigned role, making it easy to give users only the amount of access they need to perform their job duties.
- Integrated identity management (hybrid identity) enables you to maintain control of users’ access across internal datacenters and cloud platforms, creating a single user identity for authentication and authorization to all resources.
- Azure Active Directory, a comprehensive identity and access management cloud solution, helps secure access to data in applications on site and in the cloud, and simplifies the management of users and groups.
- Cloud App Discovery is a premium feature of Azure Active Directory that enables you to identify cloud applications that are used by the employees in your organization.
- Azure Active Directory Identity Protection is a security service that uses Azure Active Directory anomaly detection capabilities to provide a consolidated view into risk detections and potential vulnerabilities that could affect your organization’s identities.
- Azure Active Directory Domain Services enables you to join Azure VMs to a domain without the need to deploy domain controllers.
- Azure Active Directory B2C is a highly available, global identity management service for consumer-facing apps that can scale to hundreds of millions of identities and integrate across mobile and web platforms.
- Azure Active Directory B2B Collaboration is a secure partner integration solution that supports your cross-company relationships by enabling partners to access your corporate applications and data selectively by using their self-managed identities.
- Azure Active Directory Application Proxy provides SSO and secure remote access for web applications hosted on-premises.



